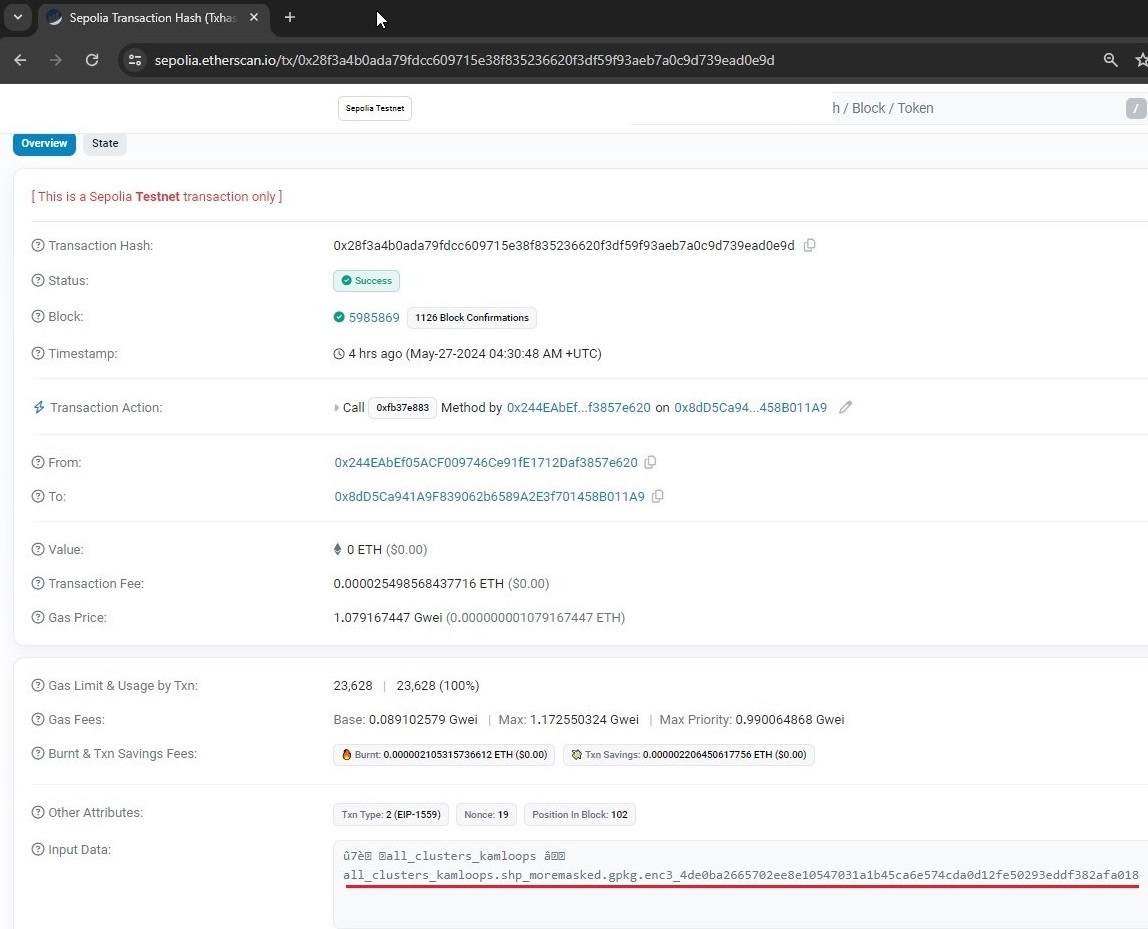
Verification
During verification, the data recipient, upon receiving the encrypted volume and encrypted passphrase, first needs to decryt the passphrase using their privte key. They also use the Shield passphrase Tab, and specify their private key and encrypted passphrase files. The Verification tab allows data recipeints to verify and decrypt the encrypted volume (that contains the original and/or obfuscated datasets).
This tab permits these tasks:
Passphrase Decryption
The Decrypt Passphrase option from the Shield Passphrase Tab allows data owners and recipeints to use their private key to decrpt the encrypted passphrase (see Generate Keys button).
Data recipients can use their private key to decrypt the encrypted passphrase, that can then be used to decrypt the dataset (see Decrypt Passphrase option in Figure 5). The private key is restricted within QGIS during decryption. Depending on security requirements, recipients can choose to send a new public key for encrypting the passphrase for each encrypted dataset or use the same one for all datasets to be sent to them.
Verification
The verification process involves proving that the encrypted volume is the same as when it was safeguarded. This is achieved by comparing the digital signatures of the encrypted volume: the current one against that stored on the Blockchain. Once they match, the user can be confident that the encrypted volume has not been altered and can proceed to decrypt the volume. These processes are explained below.
The recipient chooses the encrypted volume and its hash value is generated and displayed. Using this value the volume's authenticity can be verified by comparing with the hash value minted on the blockchain.
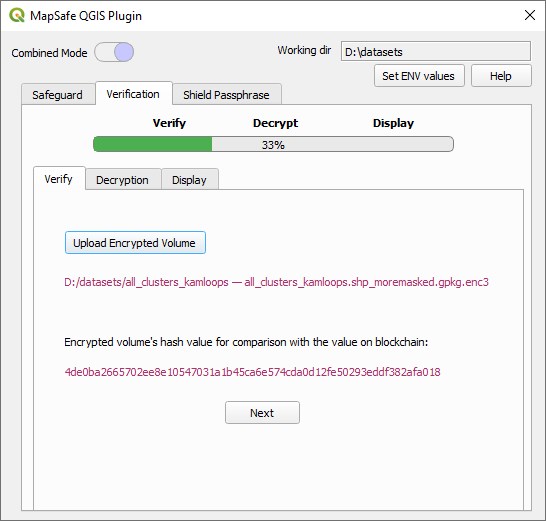
This value is then compared with that stored on the Blockchain under the users account. The masked dataset is encrypted in the browser memory at three levels. If both hash values match, it can be assured that the encrypted volume is the same as when it was safeguarded.